8 Essential Email Security Best Practices for 2025
Discover 8 essential email security best practices to protect your inbox. Learn about MFA, encryption, DMARC, and more to stop phishing and data breaches.

Email remains the backbone of professional communication, but it's also the most exploited entry point for cyberattacks. From sophisticated phishing schemes to data-stealing malware, the threats are constant and evolving. Simply relying on a strong password is no longer sufficient to protect your sensitive information. This guide provides a comprehensive roundup of the most essential email security best practices designed to fortify your defenses. For small and mid-sized businesses, understanding the latest threats and adopting robust defenses is crucial. Learn more about these critical email security best practices to gain deeper insights tailored for SMEs.
We'll move beyond generic advice to offer actionable, detailed strategies that you can implement immediately. This article covers everything from establishing robust authentication protocols like SPF, DKIM, and DMARC to fostering a security-first culture through effective anti-phishing training. You will learn how to properly configure multi-factor authentication (MFA), leverage email encryption, and conduct regular security audits. Implementing these measures will transform your inbox from a vulnerable target into a hardened fortress, safeguarding your most sensitive data and communications from unauthorized access and attacks.
1. Multi-Factor Authentication (MFA)
One of the most impactful email security best practices you can implement is enabling Multi-Factor Authentication (MFA). MFA, sometimes called two-factor authentication (2FA), acts as a powerful secondary defense for your account. Instead of relying solely on a password, which can be stolen or guessed, MFA requires you to provide a second piece of evidence to prove your identity. This drastically reduces the risk of unauthorized access.
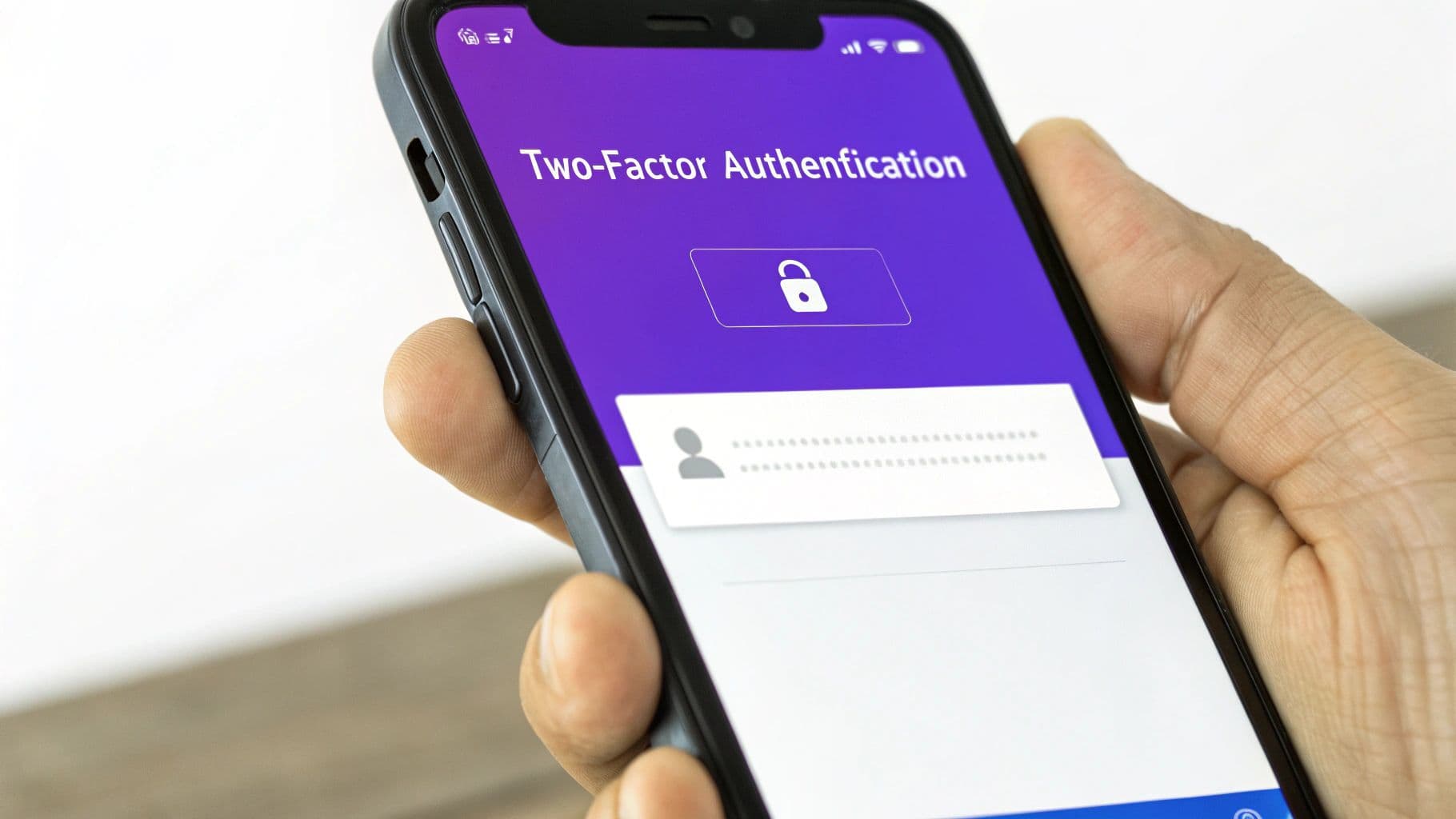
The principle is simple: combine something you know (your password) with something you have (like your phone) or something you are (like your fingerprint). Even if a cybercriminal successfully phishes your password, they are stopped in their tracks because they do not possess your secondary verification factor. The effectiveness of this approach is well-documented; Google reported that adding an SMS recovery phone number to accounts blocked 100% of automated bots, 99% of bulk phishing attacks, and 76% of targeted attacks.
How to Implement MFA Effectively
To get the most out of MFA, consider these actionable tips:
- Prioritize App-Based Authenticators: While SMS codes are better than nothing, they are vulnerable to SIM-swapping attacks. Use dedicated authenticator apps like Google Authenticator, Microsoft Authenticator, or Authy for more secure, time-based one-time passwords (TOTP).
- Secure Your Backup Codes: When you set up MFA, you will be given backup codes for account recovery. Store these codes offline in a secure location, such as a locked safe or a password manager, so you can regain access if you lose your primary device.
- Leverage Adaptive Authentication: For businesses, implement adaptive or risk-based MFA. These systems can require extra verification steps only when a login attempt seems risky, such as from an unrecognized device or a new geographic location, creating a smoother user experience.
If your email access is part of a hands-free workflow, it's vital to ensure your security doesn't get in the way. For professionals using voice-activated tools like Harmony AI to manage their inbox on the go, a single secure login session protected by MFA provides peace of mind. This allows you to stay productive while commuting or during a workout, knowing your account is fortified against intrusion. To dive deeper into setting up this crucial layer of defense, you can learn more about configuring Multi-Factor Authentication.
2. Email Encryption
While firewalls and secure passwords protect your accounts, email encryption is what protects the actual content of your messages. Encryption is the process of converting your readable email text into a scrambled, coded format. Only the intended recipient with the correct decryption key can unlock and read the message, ensuring your sensitive information remains confidential both while in transit across the internet and while sitting in a server.

This practice is non-negotiable for industries handling private data, such as healthcare organizations using S/MIME or PGP for HIPAA compliance or legal firms protecting attorney-client privilege. The importance of end-to-end encryption was famously highlighted by whistleblower Edward Snowden. Today, providers like ProtonMail have made this high-level security accessible to everyone, and major platforms like Microsoft 365 and Google Workspace offer powerful, often automated, encryption tools for businesses. Implementing robust email encryption is a cornerstone of modern email security best practices.
How to Implement Email Encryption Effectively
To properly secure your communications, consider these practical steps:
- Enable Transport Layer Security (TLS): At a minimum, ensure your email provider uses TLS. This encrypts the connection between email servers, preventing eavesdropping as messages travel. It is the baseline standard for secure email transit.
- Implement End-to-End Encryption (E2EE): For maximum security, use E2EE tools like PGP (Pretty Good Privacy) or S/MIME (Secure/Multipurpose Internet Mail Extensions). This ensures only the sender and recipient can ever read the email content.
- Automate Encryption Policies: In a business environment, configure your email gateway to automatically encrypt emails containing sensitive keywords or patterns, like "social security number" or "credit card," before they leave your network. This removes the risk of human error.
- Establish Key Management Procedures: Securely storing and managing encryption keys is critical. Use a trusted key server or a secure internal process for distributing public keys and protecting private keys.
For professionals on the move, securing communications is vital. When using voice-activated tools like Harmony AI to manage your sensitive emails hands-free, you can trust that your underlying email service’s encryption is protecting the content of your messages. This allows you to dictate confidential replies during your commute or between meetings, knowing the information is shielded from interception. To learn more about how encryption works, check out this guide on Email Encryption.
3. Anti-Phishing Training and Awareness
Technical defenses are essential, but one of the most critical email security best practices addresses the human element: Anti-Phishing Training. Since employees are often the first line of defense, educating them to recognize and report suspicious emails is paramount. Phishing attacks rely on social engineering to trick users into revealing sensitive information or deploying malware. A well-trained workforce can transform your biggest vulnerability into your strongest security asset.
The power of this human-centered approach is proven. Security awareness training leader KnowBe4 has shown that consistent training can reduce an organization's susceptibility to phishing by up to 87%. Similarly, Google’s rigorous internal training program has successfully diminished employee clicks on phishing links to a fraction of a percent. This demonstrates that investing in user education yields a tangible and significant return by preventing breaches before they happen.
How to Implement Anti-Phishing Training Effectively
To build a resilient human firewall, consider these actionable strategies:
- Start with a Baseline Simulation: Before training begins, send a simulated phishing email to gauge your team's current awareness level. This provides a clear benchmark to measure the effectiveness of your program over time.
- Make Training Relevant and Continuous: Use real-world examples of current phishing threats that are relevant to your industry and users' daily tasks. Instead of a one-time annual session, provide ongoing, bite-sized training and regular simulations to keep security top-of-mind.
- Provide Immediate, Actionable Feedback: When a user clicks on a simulated phishing link, provide immediate feedback explaining what the red flags were. Conversely, reward employees who correctly identify and report suspicious emails to encourage good security behavior.
For professionals who manage their inbox on the move, staying vigilant is key. Tools like Harmony AI help by allowing you to safely review and triage emails with voice commands, reducing the temptation to hastily click on links while distracted. By combining this hands-free efficiency with robust anti-phishing knowledge, you can maintain both productivity and security, ensuring your focus remains on legitimate tasks. To see how a leader in this space operates, you can learn more about KnowBe4's security awareness training.
4. Email Gateway Security Solutions
A powerful, business-grade email security best practice is to deploy an advanced email gateway. Think of it as a fortified checkpoint for all your email traffic. This solution sits between the internet and your email server, meticulously inspecting every incoming and outgoing message to detect and block malicious content, spam, malware, and sophisticated phishing attempts before they ever have a chance to reach a user’s inbox.

These gateways use a layered defense approach, combining signature-based detection for known threats, heuristic analysis for suspicious behavior, and increasingly, AI-powered engines to identify novel attacks. Industry leaders like Proofpoint, Microsoft Defender for Office 365, and Barracuda showcase the effectiveness of this model. For instance, Proofpoint protects a significant portion of Fortune 100 companies, while Mimecast provides critical email continuity, ensuring business operations continue even during an outage.
How to Implement Email Gateway Security Effectively
To maximize the protection offered by an email gateway, focus on strategic configuration and maintenance:
- Deploy Both Inbound and Outbound Filtering: While inbound filtering protects your organization from external threats, outbound filtering is crucial for preventing data breaches and stopping compromised internal accounts from spreading malware to clients and partners.
- Regularly Update Threat Intelligence: Your gateway's effectiveness depends on its knowledge of the latest threats. Ensure that its threat intelligence feeds are configured to update automatically and frequently to stay ahead of emerging attack vectors.
- Configure and Monitor Quarantine Policies: Set clear policies for what happens to suspicious emails. Monitor quarantined messages and tune your system to minimize false positives (legitimate emails being blocked) and false negatives (threats getting through).
For professionals who are constantly on the move, a secure email gateway provides a foundational layer of defense that works silently in the background. This ensures that the inbox you access with voice-activated tools like Harmony AI is pre-filtered and significantly safer. This lets you manage communications hands-free during a commute or workout, trusting that a robust security shield has already neutralized most threats. To see how a secure, hands-free workflow can transform your productivity, explore the capabilities of Harmony AI.
5. Regular Security Audits and Monitoring
Defending against cyber threats is not a one-time setup; it requires constant vigilance. One of the most critical email security best practices is implementing regular security audits and continuous monitoring. This proactive approach involves systematically evaluating your email systems, policies, and user behaviors to identify vulnerabilities before they can be exploited. It transforms security from a static checklist into a dynamic, responsive process.
This practice is essential because the threat landscape is constantly changing. New attack methods emerge, software vulnerabilities are discovered, and internal configurations can drift over time. Regular audits, as championed by standards like NIST and ISO 27001, provide a periodic, in-depth look at your security posture, while continuous monitoring offers real-time awareness of potential threats. For example, financial institutions conduct quarterly assessments to ensure compliance and fortify defenses, a model any security-conscious organization can adopt.
How to Implement Audits and Monitoring Effectively
To build a robust audit and monitoring framework, consider these actionable tips:
- Establish a Consistent Schedule: Don't wait for an incident to occur. Schedule comprehensive security audits at regular intervals, such as quarterly or annually. Use a combination of internal teams for routine checks and external auditors for an unbiased, expert perspective.
- Automate Real-Time Monitoring: Deploy tools that continuously monitor email traffic for anomalies. Integrating your email security gateway with a Security Information and Event Management (SIEM) system allows for the correlation of alerts from multiple sources, providing a clearer picture of potential threats.
- Document and Remediate: Meticulously document all findings from your audits. Create a clear action plan with assigned responsibilities and deadlines to remediate any identified weaknesses. This creates a cycle of continuous improvement.
For professionals who rely on constant, secure access to their inbox, this behind-the-scenes diligence is what enables safe, hands-free workflows. When using a voice-activated assistant like Harmony AI to manage emails during a commute or workout, you can operate with confidence. You know that robust monitoring and regular audits are working in the background to keep the communication channel secure, allowing you to focus on your productivity without interruption.
6. Strong Password Policies and Management
A strong password serves as the primary gatekeeper for your email account, but relying on memory alone is no longer a viable strategy. Implementing comprehensive password policies and using dedicated management tools form the foundational layer of your email security. This approach shifts the burden from users remembering complex, unique passwords for every service to a system that automates their creation, storage, and retrieval securely.
The effectiveness of this method is evident in its widespread adoption. Password managers like 1Password and LastPass are trusted by hundreds of thousands of businesses and millions of users to protect digital credentials. These tools solve the password paradox: the need for credentials to be both impossibly complex for attackers to guess and effortlessly simple for users to access. Modern guidelines from NIST (SP 800-63B) have also evolved, now emphasizing length and uniqueness over forced complexity and frequent, mandatory changes.
How to Implement Strong Password Policies Effectively
To build a robust password defense, integrate these actionable best practices:
- Prioritize Length and Uniqueness: Encourage the use of long passphrases (e.g., "Correct-Horse-Battery-Staple") over short, complex strings (e.g., "P@55w0rd!"). A long, memorable phrase is significantly harder to crack and easier for users to manage. Ensure every account has a completely unique password.
- Deploy a Corporate Password Manager: Provide your team with licenses for a reputable password manager. This not only encourages strong password habits but also provides a secure way to share credentials when necessary and allows for centralized oversight and policy enforcement.
- Monitor for Breached Credentials: Use services that monitor the dark web for compromised credentials associated with your company's domain. Tools like Have I Been Pwned's domain search can proactively alert you if an employee's password appears in a data breach, allowing you to respond immediately.
- Eliminate Mandatory Password Expiration: Move away from arbitrary 90-day password change policies. NIST now recommends changing passwords only when there is evidence of compromise. This prevents "password fatigue," where users make small, predictable changes that weaken security.
For busy professionals who rely on voice commands to manage their inbox, robust password security is non-negotiable. With Harmony AI, a single, secure sign-on protected by a strong, unique password stored in a manager allows for seamless, hands-free productivity. You can confidently manage emails while on the move, knowing the entry point to your digital life is properly fortified against common attacks. Learn more about creating un-guessable passwords by checking out this guide on passphrase creation.
7. Email Authentication Protocols (SPF, DKIM, DMARC)
To truly secure your email domain from impersonation, you must implement a trio of powerful email authentication protocols: SPF, DKIM, and DMARC. These standards work together to verify that an email claiming to be from your domain is legitimate, effectively preventing cybercriminals from spoofing your address. This is a crucial email security best practice that protects your brand reputation and prevents your domain from being used in phishing attacks against your customers, partners, and the public.
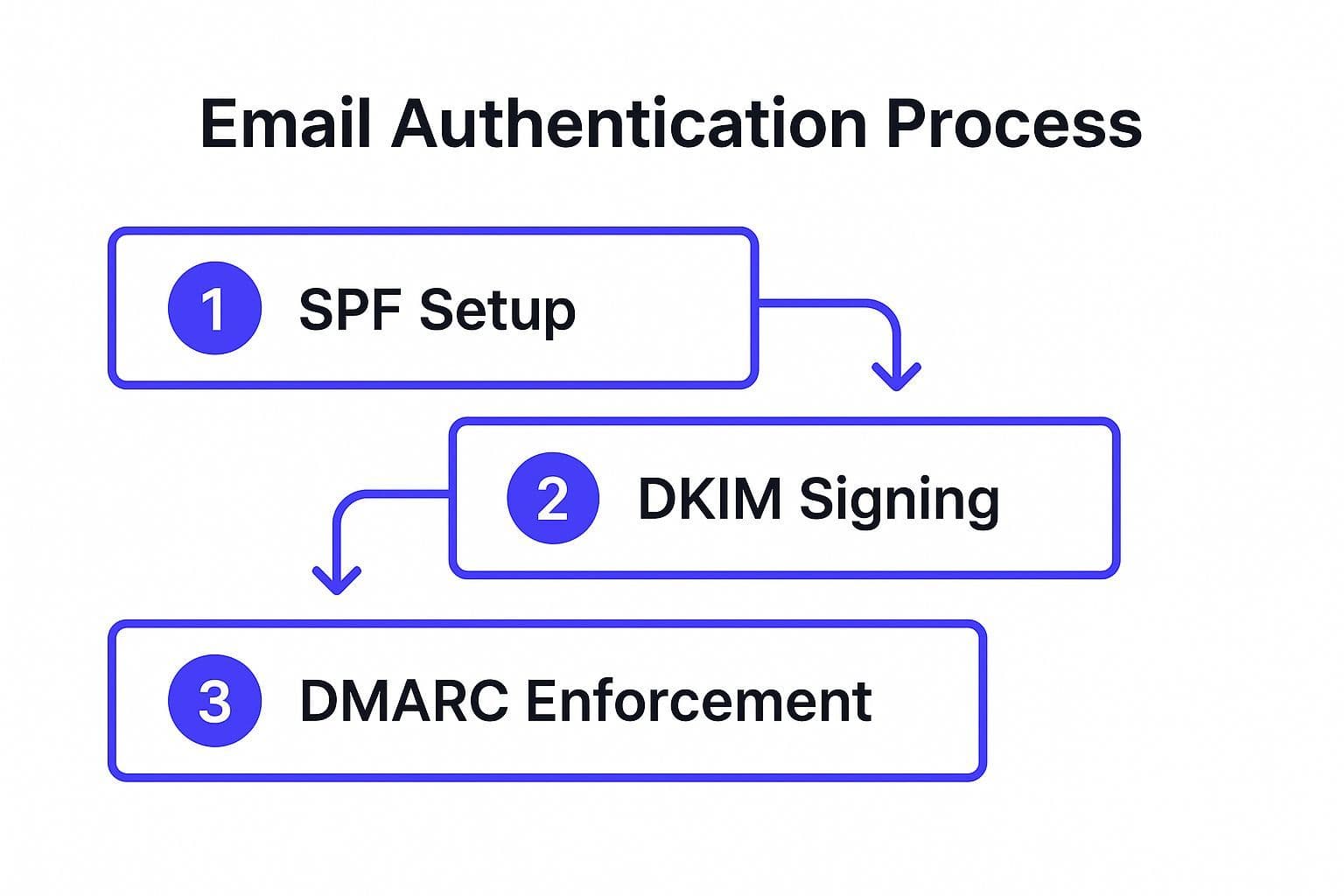
This process flow diagram illustrates the recommended implementation path for total email authentication. Starting with SPF, then layering on DKIM, and finally enforcing policy with DMARC creates a robust defense against spoofing. Following this sequence ensures that each protocol builds upon the last, providing comprehensive protection without disrupting legitimate email flow.
The power of this trifecta is undeniable. When PayPal implemented a strict DMARC policy, it reported blocking over 99.9% of fraudulent emails spoofing its domain. Similarly, recent requirements from Google and Yahoo mandate that bulk senders use these protocols to ensure email delivery, solidifying them as an industry standard for trust and security.
How to Implement Email Authentication Effectively
Deploying these protocols requires a methodical approach. Follow these actionable steps to fortify your domain:
- Start with a Monitoring Policy: Begin your DMARC implementation in "monitor-only" mode (). This allows you to receive reports on all emails sent using your domain, both legitimate and fraudulent, without affecting email delivery.
- Analyze and Authorize Sources: Use the DMARC aggregate reports to identify all legitimate services sending email on your behalf (e.g., marketing platforms, CRM systems, support desks). Ensure each one is properly configured with SPF and DKIM.
- Gradually Enforce Your Policy: Once you are confident that all legitimate mail is authenticated, gradually increase your DMARC policy's strength. Move from to (which sends unauthenticated mail to spam) and finally to (which blocks it outright).
For busy professionals managing communications, knowing your domain is protected provides essential peace of mind. With your authentication protocols in place, you can confidently use tools like Harmony AI to manage your inbox via voice commands, assured that the emails you send are verified and your brand is secure. To learn more about setting up these critical defenses, you can explore the official guidance at DMARC.org.
8. Regular Software Updates and Patch Management
One of the most fundamental yet critical email security best practices is establishing a systematic process for software updates and patch management. This involves keeping all components of your email ecosystem, from servers and clients to security tools, updated with the latest software versions and security patches. Unpatched software is a primary entry point for cyberattacks, as it contains known vulnerabilities that criminals actively exploit.
Neglecting updates is like leaving your front door unlocked. Cybercriminals scan for outdated systems, and when they find one, they can often gain access using publicly known exploits. The infamous Equifax breach, which exposed the personal data of 147 million people, was a direct result of a failure to patch a known vulnerability in their web application framework. Applying updates promptly closes these security gaps, ensuring your email infrastructure remains fortified against emerging threats.
How to Implement Patch Management Effectively
To ensure your systems are consistently protected, adopt these actionable strategies for updates:
- Establish a Routine: Schedule regular maintenance windows for applying updates, such as following Microsoft's monthly "Patch Tuesday" cycle. Consistency is key to preventing security drift.
- Test Before Deploying: Always test patches in a non-production or staging environment first. This helps identify any potential conflicts or operational issues before rolling them out across your live systems.
- Prioritize Critical Patches: Not all patches are equal. Subscribe to vendor security advisories (e.g., from Microsoft, Google, or Red Hat) to stay informed about critical vulnerabilities and deploy those patches immediately.
- Automate Where Possible: Use automated patch management and vulnerability scanning tools to maintain a complete inventory of your software and identify missing updates. This reduces manual effort and minimizes human error.
This disciplined approach ensures that the applications you rely on are secure from the ground up. For professionals who use voice-command tools like Harmony AI to manage their inbox hands-free, this backend security is paramount. Knowing your email client and server are fully patched allows you to dictate messages and manage your schedule with confidence, whether you're driving or multitasking at home, assured that your foundational systems are secure.
Email Security Best Practices Comparison Table
| Item | Implementation Complexity 🔄 | Resource Requirements ⚡ | Expected Outcomes 📊 | Ideal Use Cases 💡 | Key Advantages ⭐ |
| Multi-Factor Authentication (MFA) | Moderate - involves multiple factors and backup methods | Moderate - requires authentication apps, tokens, or devices | Strong reduction in unauthorized access and phishing (e.g., 99% phishing reduction by Google) | Protecting accounts with weak passwords; compliance needs | High security enhancement; relatively easy to deploy |
| Email Encryption | High - key management and compatibility complexity | High - requires encryption tools and user training | Confidentiality of email content; compliance with GDPR, HIPAA | Transmitting sensitive data; regulated industries | Ensures data privacy and message integrity |
| Anti-Phishing Training and Awareness | Low to Moderate - ongoing training and simulation efforts | Low - mainly organizational time and tools | Significant reduction in phishing success; improved user behavior | Organizations aiming to strengthen human defense layer | Cost-effective; measurable behavioral improvements |
| Email Gateway Security Solutions | High - integration of advanced filtering and tuning | High - infrastructure, subscriptions, ongoing management | Blocks threats before user impact; reduces malware and spam | Enterprise environments with high email volume | Centralized protection; detailed threat visibility |
| Regular Security Audits and Monitoring | High - requires expert resources and continuous effort | High - skilled personnel and monitoring tools | Early threat detection; compliance assurance; policy effectiveness | Regulated sectors and large organizations | Proactive vulnerability identification; continuous security improvements |
| Strong Password Policies and Management | Low to Moderate - policy setup plus user adoption efforts | Moderate - password managers and administration | Reduced password-based attacks; improved account security | All organizations as foundational security measure | Enhances baseline security; supports compliance |
| Email Authentication Protocols (SPF, DKIM, DMARC) | High - DNS setup, coordination, and phased rollout | Moderate - technical expertise and monitoring tools | Prevents domain spoofing; improves email deliverability | Brand protection; preventing impersonation attacks | Reduces phishing and spoofing; improves trust |
| Regular Software Updates and Patch Management | Moderate - scheduling, testing, and deployment procedures | Moderate to High - IT resources and automation tools | Closes vulnerabilities; maintains system stability and security | Critical email infrastructure maintenance | Essential for vulnerability management and compliance |
Moving from Defense to Offense in Email Security
Navigating the complexities of digital communication requires more than just a passive, defensive stance. The comprehensive list of email security best practices detailed in this article, from implementing robust Multi-Factor Authentication (MFA) to establishing rigorous email authentication protocols like SPF, DKIM, and DMARC, forms the bedrock of a formidable security posture. We have explored the critical layers that protect your inbox, transforming it from a potential vulnerability into a secure, reliable tool for professional and personal communication.
The journey doesn’t end with a one-time setup. True digital resilience is an active, ongoing process. Think of it as evolving from building a fortress to actively patrolling its perimeter. The initial setup of strong passwords, consistent software updates, and advanced email gateway solutions are your foundational walls. However, the real strength comes from continuous vigilance, such as conducting regular security audits, providing ongoing anti-phishing training, and consistently monitoring for anomalous activity. Each practice works in concert with the others, creating a layered defense where one control compensates for the potential shortcomings of another.
Synthesizing Your Security Strategy
The core takeaway is that isolated security measures are insufficient. A truly effective strategy integrates technical controls with human awareness. For instance, even the most advanced email gateway can be circumvented by a sophisticated, socially engineered phishing attack. This is where your investment in employee training pays dividends, turning your team into an alert, human firewall.
Your actionable next steps should be to:
- Audit Your Current Defenses: Systematically review your existing security measures against the best practices outlined. Where are the gaps? Is MFA enabled on all critical accounts? Are your DMARC policies set to ?
- Prioritize Implementation: You may not be able to implement everything at once. Start with the highest-impact items, such as enforcing strong, unique passwords with a password manager and enabling MFA across your organization.
- Cultivate a Security-First Culture: Make security a shared responsibility. Regular, engaging training sessions and clear communication about emerging threats empower every user to become a proactive defender of their own inbox and the organization's data.
Harmony AI: Secure Productivity for the Modern Professional
Mastering these email security best practices does more than just prevent data breaches; it builds a foundation of trust and enables greater productivity. When you are confident in the security of your communications, you can focus on efficiency and innovation. This is where modern tools can enhance your workflow without compromising the security you have worked so hard to build.
For professionals constantly on the move, from commuting parents to field workers, accessing email securely and efficiently is paramount. This is where voice-enabled assistants can bridge the gap. Harmony AI is an AI-powered personal assistant designed with a privacy-first approach, allowing for hands-free management of your Gmail and Google Calendar. It operates with end-to-end TLS encryption and undergoes regular third-party security audits, aligning perfectly with the principles of a robust security framework. By integrating such secure productivity tools, you move beyond simple defense and begin to leverage technology to work smarter and safer, ensuring your digital communications are protected, whether you are at your desk or on the go.
Ready to enhance your productivity without sacrificing security? Discover how Harmony AI allows you to manage your email and calendar hands-free, built with end-to-end encryption and a commitment to your privacy. Visit Harmony AI to learn how to securely reclaim your time and streamline your workflow.
Harmony - AI Planner
Plan your weeks, plan your life. Define your mission, plan weeks around your roles, and stay on track every day with AI guidance.
Download FreePersonal Mission
Define your deeper why
Weekly Planning
Role-based goal setting
AI Guidance
Smart suggestions & nudges
Celebrations
Stay motivated daily